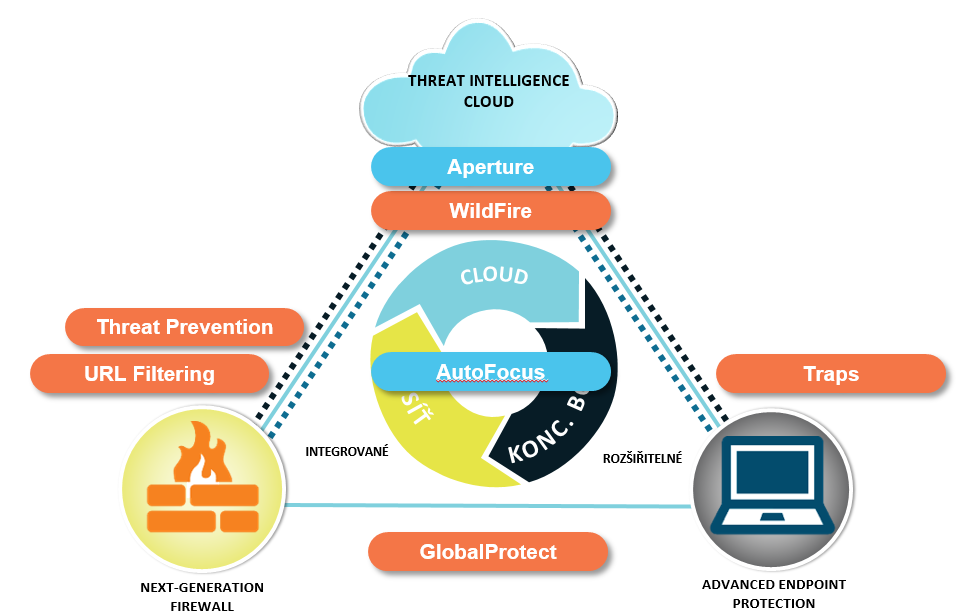
traps
Exploit Mitigation
Traps™ focuses on the core techniques leveraged by exploits in advanced cyberattacks. Traps renders these techniques ineffective by breaking the exploit sequence and blocking the technique the moment it is attempted.
Malicious Executable Prevention
Traps prevents executable malware by preventing core malware techniques. Additionally, policy-based restrictions can be used to reduce the endpoint attack surface, and integration with the WildFire™ threat intelligence cloud offers rapid analysis of executables before they can run.
Lightweight yet Comprehensive
Traps does not perform any system scanning, or rely on signature updates, the way many endpoint solutions do. This approach results in minimal impact to the user experience and system-level resources while protecting all applications, including proprietary and third-party ones.